How to Master Security on Social Media
“Following the Cambridge Analytica and Facebook scandal - how do you stay safe online?”
by Virginie Roux | 22nd March 2018

Nowadays, Social Media sites form an integral part of our lives to stay in touch and communicate with friends and interact with other people on the web. But as harmless as they seem, they can put users’ security at risk because of poor practices.
“Your online presence leaves an eternal footprint on the World Wide Web – learn to manage it better!”
The recent Cambridge Analytica scandal is an unfortunate representation of data security failure on social media. In 2014, Facebook users took part in a personality quiz entitled: “This is your Digital Life” by Cambridge University Researcher, Dr Aleksandr Kogan. The online quiz not only permitted the harvest of responders’ private information but also the gathering of public information belonging to their Facebook friends, collecting data from about 50 million users. This data was passed on Cambridge Analytica and was maliciously exploited for psychographic profiling. Some consider that it may have played a major part in the victory of Donald Trump during his 2016 US elections campaign, as Cambridge Analytica is suspected to have delivered pro-Trump information to voters based on their psychological profile.
However, you are personally responsible for what information you put out on the Internet, so you should be careful about what you publish online. Compromising pictures of you drinking with friends, your political views, a controversial opinion, or even comments about your employers can all damage your reputation or the image of the company you represent. Once it is posted and content is shared, there is little you can do!
On the other hand, leaving personal information out in the open, make you an easy target for computer hackers. Cyber criminals can use details such as your date of birth, your mother’s name, or the name of your former school that you display publicly online, to bypass security questions and gain access to your bank account or guess part of your password.
Furthermore, the risk is elevated when you tag yourself at a location on Facebook or Instagram, indicating where you are in real time. Although, it can be tempting for you to show your friends what you do during your holidays, you may not be so thrilled at the idea of telling burglars that you are absent, and that your house is therefore empty. Conversely, high-profile individuals such as celebrities who reveal where they are on social media, put themselves in danger. This was the subject of a recent article published on our blog, entitled ‘Social Media, your ego and security…’, which looked into the Kim Kardashian’s robbery case as an example of security breach.
Nevertheless, we are not advising you to cease posting on social media or delete your account, but we would like to give you instead some guidance as to how to use social network sites safely. Here is how to do it!

Lock Down Your Profile
When creating their social media profile, certain people often forget to check their privacy settings, before they complete their profile and post content. Unfortunately, default settings that are applied automatically, usually give users a very low protection level.
As a result, it is important to review the restrictions you can implement on your account, to ensure that your information don’t end up in the wrong hands! Anything you display in your bio should be hidden from the public and only viewable by your friends/connections, like your location, your education details and date of birth.
Furthermore, the audience of your posts and photos should be set, so only your friends/connections can see them. You can even limit your audience for certain posts, in order that only a restricted list of people sees what you post.
Finally, protecting your pictures is another preventive measure against cyber criminals, who could steal your photos to create a new profile to impersonate you. Impersonation is indeed one of the most common forms of social engineering on social media. This vicious tactic is ingenious in the sense that Internet users are more likely to trust someone they know than a stranger. Social engineers who employ these manoeuvres, can gain access to your private information and send victims messages asking for financial help. The best thing to do if you have any doubt regarding the authenticity of a new contact, is to pick up the phone to your friend to check that the profile is indeed genuine.
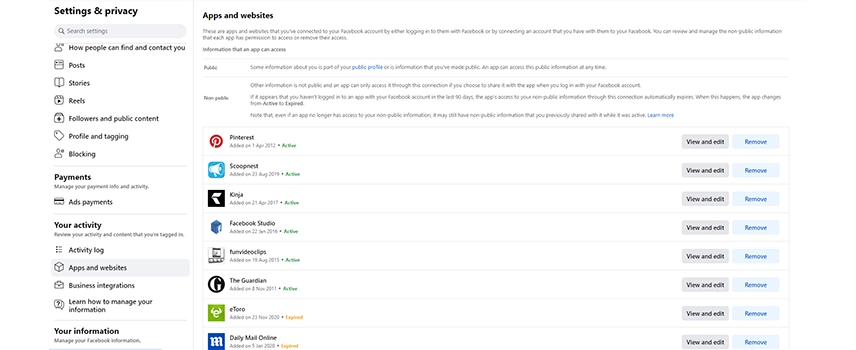
Restricted Access To External Apps
As demonstrated by the Cambridge Analytica scandal, App developers can gain access to users’ private details on social media and could potentially exploit personal data for their own use.
Although it is convenient to use Facebook or Google to log in to applications or third-party sites without having to create an account, you should review what information you are sharing from your social account with an external application and set up restrictions.
For instance, Facebook can by default share very detailed information about you with other applications, such as: your public profile, friend list, status updates, home town, current city, photos uploaded by you and photos you’re tagged in, likes and your email address. They can as well send you notifications and post on your behalf.
To ensure better control of your information, review the App settings page of your social profile where all the third-party applications are listed and edit the settings of each single applications to make data unavailable to them or revoke them access if necessary.
Secure Login
When joining a social network site, we recommend choosing a unique password that is strong and unfathomable, combining the use of upper and lower-case letters, numbers and symbols, with 8 characters minimum. If you are worried about not having a strong enough password, a password generator is a simple way to secure your login.
Besides, passwords should be changed frequently in case it gets compromised. You may be reluctant to follow these measures for fear of forgetting it, or because it’s not easy to type from memory. To go around this, you should keep an up-to-date master list of all your passwords on an Excel document that you can encrypt with a password, limiting access to your document.
Alternatively, you can use a password manager such as the like of “Last Pass”, which has a built-in system that generates password randomly and save all your passwords for you.
Moreover, to add an extra layer of security to your social media accounts, the use of a two-factor authentication will be a stumbling block to computer hackers. When you log in to your social account, you will receive a text on your phone with a code to type in, before you enter your password.
On certain sites, you have the possibility to also get an alert about unrecognised logins, which is another measure you can take to further enhance your security.
Moreover, to add an extra layer of security to your social media accounts, the use of a two-factor authentication will be a stumbling block to computer hackers. When you log in to your social account, you will receive a text on your phone with a code to type in, before you enter your password.
On certain sites, you have the possibility to also get an alert about unrecognised logins, which is another measure you can take to further enhance your security.
Delete Old Social Media Profiles
With the surge of social media sites, it sometimes is difficult to keep track of the many accounts we have on different platforms and remember all the sites we signed up to. We may stop using certain applications and forget about their existence. The issue is that an account that is left inactive is prone to being targeted by computer hackers, as their criminal activity will stay undetected by yourself if they hack you.
So, how do you find again all the sites you subscribe to? A quick way for you to monitor your online social media presence is to perform a Google Search with your name, this should give you a quick overview of the sites you are on. If you are an avid user of social media and use a Gmail or an Outlook account to log in to sites, you can quickly monitor your social media subscriptions by using “Deseat.me”; this application will display an exhaustive list of your profiles and will enable you to delete the accounts you don’t want to keep.
Despite all our recommendations, you can hope for the best in the near future! To comply with the General Data Protection Regulation (GDPR) coming into effect in the EU in May, social networks will have to give users better control of their personal data, ensuring improved data privacy protocols for consumers. Thus, the law won’t only apply to EU businesses but will concern enterprises worldwide that handle and process the data of people in the EU.
Therefore, 2018 is a turning point in terms of cyber security, so take back the power that was yours to have!